Leet Chrome bug finders can bag $1337 reward from Google
Updated: 2010-01-29 17:08:17
 Google has launched a new initiative to encourage vulnerability researchers to report any security holes they find in the Google Chrome browser.
Anyone who find a bug in Chrome or Chromium, the open source code used as the foundations of Chrome, can receive between $500 and $1337 for reporting the problem to Google.
Bugs felt to be [...]
Google has launched a new initiative to encourage vulnerability researchers to report any security holes they find in the Google Chrome browser.
Anyone who find a bug in Chrome or Chromium, the open source code used as the foundations of Chrome, can receive between $500 and $1337 for reporting the problem to Google.
Bugs felt to be [...]
 Yesterday, Mozilla released the latest version of its web browser Firefox and it comes with a rather nice-sounding security feature.
Firefox 3.6 claims to be faster than ever before, but that's not why it's caught my attention. The new functionality that I'm pleased to hear about is its ability to detect out-of-date plugins.
Plugins are those [...]
Yesterday, Mozilla released the latest version of its web browser Firefox and it comes with a rather nice-sounding security feature.
Firefox 3.6 claims to be faster than ever before, but that's not why it's caught my attention. The new functionality that I'm pleased to hear about is its ability to detect out-of-date plugins.
Plugins are those [...] In my last post I mentioned that the “Operation Aurora” exploit code was public and that we could expect other attacks leveraging the CVE-2010-0249 exploit to emerge. Given the significance of the recent earthquake in Haiti, and the slew of phishing sites, email scams, etc; it makes sense that attackers would try to incorporate an [...]
In my last post I mentioned that the “Operation Aurora” exploit code was public and that we could expect other attacks leveraging the CVE-2010-0249 exploit to emerge. Given the significance of the recent earthquake in Haiti, and the slew of phishing sites, email scams, etc; it makes sense that attackers would try to incorporate an [...]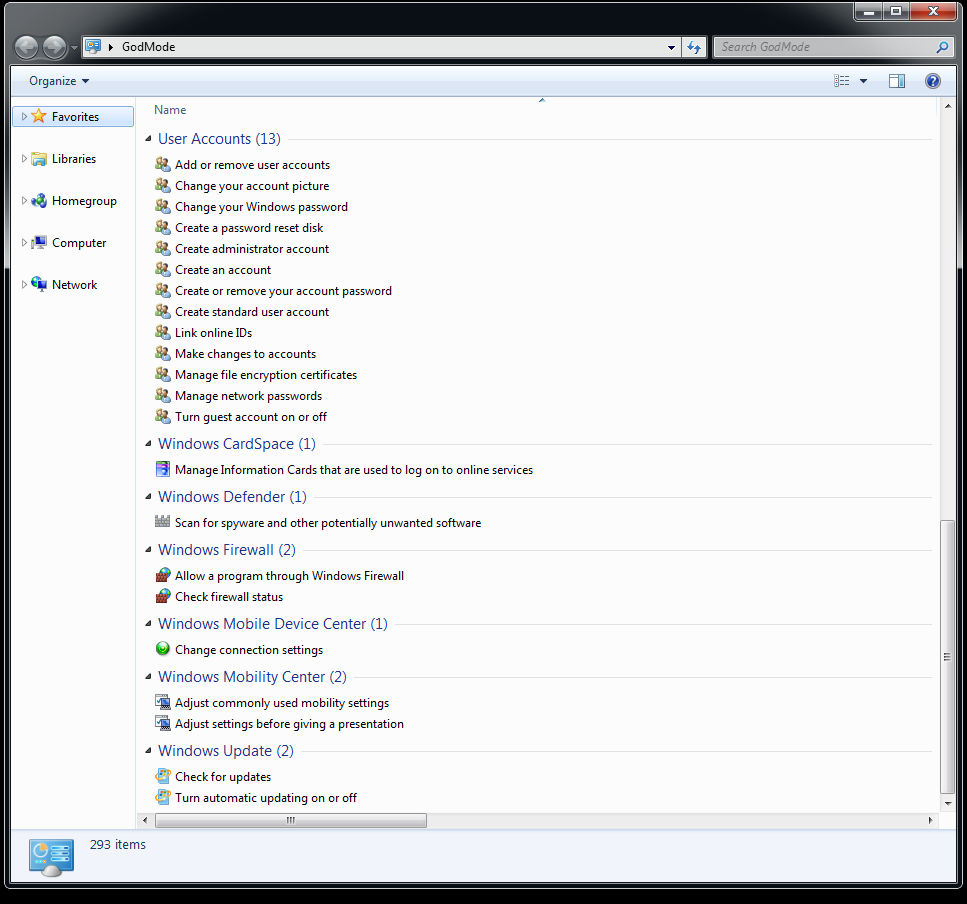 Seems the new year has brought out a few new findings. One being the newly discovered “God Mode” feature in Microsoft’s Windows 7 based operating systems. At its core, it’s basically a glorified control panel. It takes all the hard to get to, or annoying multiple right click -> properties -> options -> submenu -> [...]
Seems the new year has brought out a few new findings. One being the newly discovered “God Mode” feature in Microsoft’s Windows 7 based operating systems. At its core, it’s basically a glorified control panel. It takes all the hard to get to, or annoying multiple right click -> properties -> options -> submenu -> [...]